Your network and portfolio of business applications continually change and grow. Employees come and go. External security threats morph and expand.
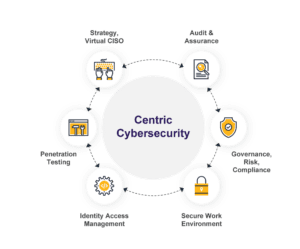
Regular penetration testing ensures that your network, applications and overall security posture is hardened against cyber attacks.
By looking at system security through the eyes of an attacker, Centric Consulting can highlight exploitable vulnerabilities, demonstrate impact and help IT teams prioritize remediation efforts. Our penetration testing consultants verify your defenses by identifying security vulnerabilities so they can be understood and solved.
Pen testing consulting services allow you to:
- Protect your sensitive data
- Comply with industry regulations that require regular pen testing and audits
- Identify vulnerabilities and gain insight into the full extent of potential flaws in your environment
- Demonstrate the potential business impact of an attack to your c-suite leaders
- Reinforce employee phishing training by exposing them to sophisticated attacks
- Test new security controls and the security of new business applications, products or services
- Test for concerns or threats specific to your business.
Our pen testing services ensure you’re prepared for new threats, save resources otherwise spent on remediating expensive breaches and provide peace of mind that your security posture has been tested.
By performing regular penetration testing, you can achieve cyber liability compliance, a clean bill of health for an application launch, a secure attestation post-critical firewall and network system changes, and compliance with various security frameworks.